To support multiple concurrent public keys per sending domain, the DNS namespace is further subdivided with "selectors". Selectors are arbitrary names below the "_domainkey." namespace. For example, selectors may indicate the names of your server locations (e.g., "mta1", "mta2", and "mta2"), the signing date (e.g., "january2005", "february2005", etc.), or even the individual user.
The most important thing is: selector indicates your DomainKeys/DKIM public key location. For example: if your domain selector is: "s1024", your public key record will be "s1024._domainkey.yourdomain"; if your domain selector is: "mta1", your public key record will be "mta1._domainkey.yourdomain".
If you have only one server and you only set the DKIM/DomainKeys on this server, you can give your selector any name. For example: your domain name is: "emailarchitect.net" and your selector is: "s1024", you should deploy your public key to "s1024._domainkey.emailarchitect.net". After the receiver received your email, the receiver can query the public key from "s1024._domainkey.emailarchitect.net" to verify your DomainKeys/DKIM signature. If you have only one server, you can skip the following sections and go to Sender Rule section directly.
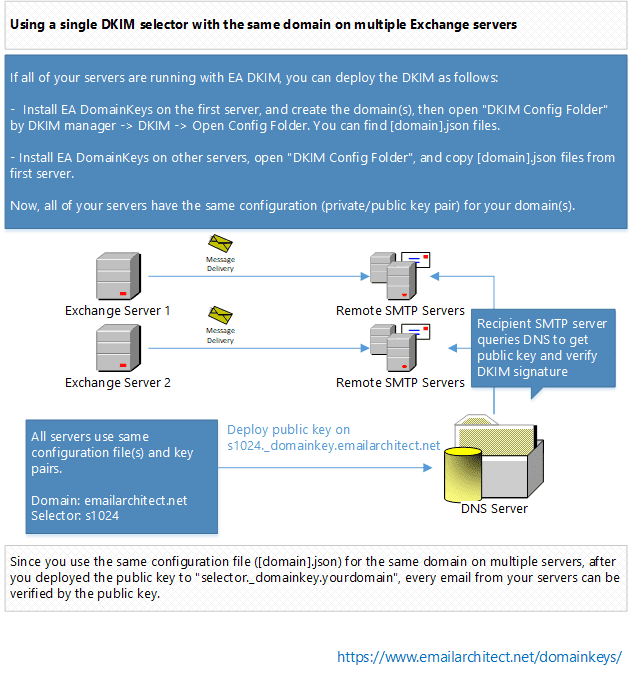
If all of your servers are running with EA DomainKeys, you should deploy the DKIM as follows:

Now, all of your servers have the same configuration (private/public key pair) for your domain.
Since you use the same configuration file ([domain].json) for the same domain on multiple servers, after you deployed the public key to "selector._domainkey.yourdomain", every email from your servers can be verified by the public key.
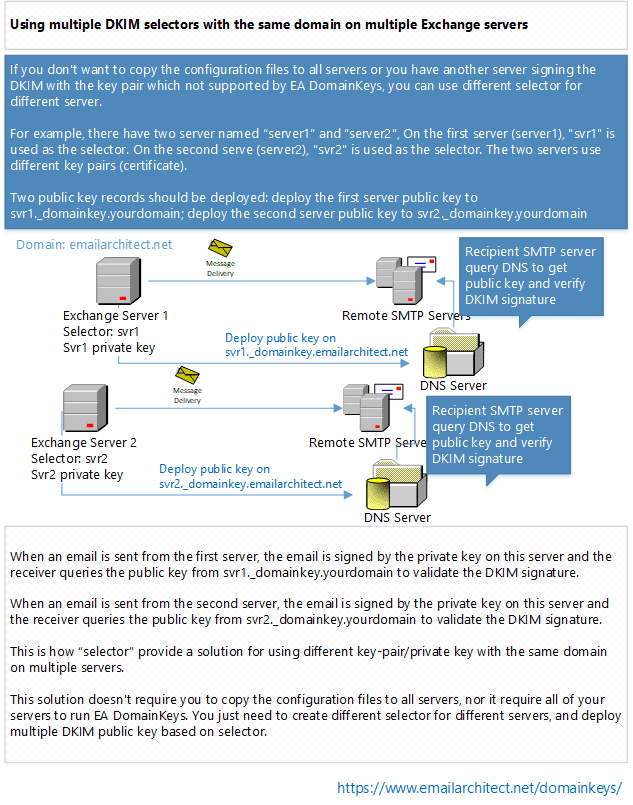
If you don't want to copy the configuration files to all servers or you have another server signing the DomainKeys/DKIM with the key pair/private key not supported by EA DomainKeys, you can use different selector for different server.
For example, there have two server named “server1” and “server2”. On the first server (server1), " svr1" is used as the selector. On the second serve (server2), "svr2" is used as the selector. The two servers use different key pairs (private key).
Two public key records should be deployed: deploy the first server public key to svr1._domainkey.yourdomain; deploy the second server public key to svr2._domainkey.yourdomain
When an email is sent from the first server, the email will be signed by the private key on this server and the receiver will query the public key from svr1._domainkey.yourdomain to validate the DKIM signature.
When an email is sent from the second server, the email will be signed by the private key on this server and the receiver will query the public key from svr2._domainkey.yourdomain to validate the DKIM signature.
This is how “selector” provide a solution for using different key-pair/certificates with the same domain on multiple servers.
This solution doesn't require you to copy the certificate to all servers, nor it require all of your servers to run EA DomainKeys. You just need to create different selector for different servers, and deploy multiple public key based on selector.
Most DKIM signers use plain text private key in PKCS8 format. To synchronize the private key in different software/signer, you can import or export pkcs8 private key in DKIM manager -> your domain - > Private Key Management.
See Also
Deploy Public Key in DNS server
Test DomainKeys/DKIM Signature
Using Sender Rule
Server Core and Installer Command Arguments
Appendix - Set up SPF record in DNS server
Appendix - Set up DMARC record
Appendix - DKIM/SPF/DMARC Inbound Authentication in Exchange Server
Appendix - Use DkimPowerShell Module in PowerShell
Online
DKIM in IIS SMTP
Service - Tutorial
DKIM in Exchange
Server 2003 - Tutorial
DKIM in
Exchange Server 2007/2010/2013/2016/2019 - Tutorial
DKIM/SPF/DMARC
Inbound Authentication in Exchange Server
Bulk Email Sender Guidelines