DomainKeys/DKIM combines of a public key cryptography and a DNS to provide credible domain-level authentication for email.
When an email claims to originate from a certain domain, DomainKeys/DKIM provides a mechanism by which the recipient system can credibly determine that the email did in fact originate from a person or system authorized to send email for that domain.
Therefore, to sign an email with DomainKeys/DKIM, you MUST have a private key/public key pair for email signing. The work flow is illustrated as follows:
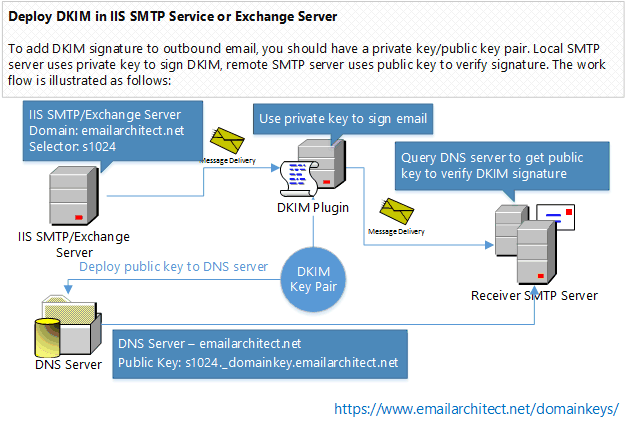
Email Sender -> IIS SMTP Service/Exchange Server -> DomainKeys/DKIM Plugin -> DomainKeys/DKIM Plugin uses the private key to create a digital signature based on the email content. -> IIS SMTP Service/Exchange Server delivers the signed email to remote recipient. Remote Server received the email -> Query the public key from the sender domain DNS record -> Verify the digital signature with public key.
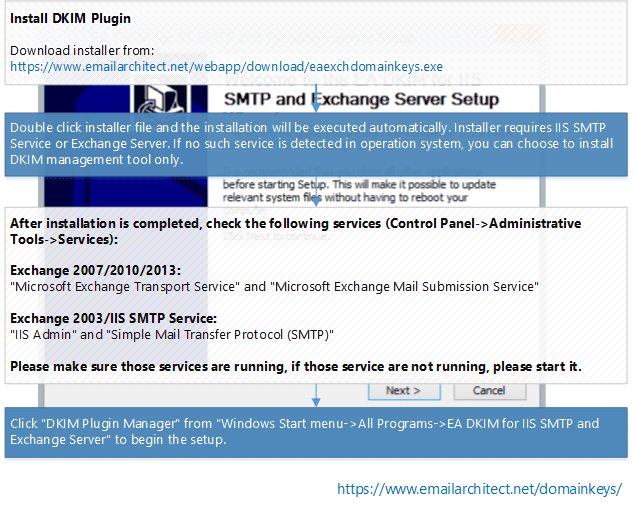
To install "EA DKIM for IIS SMTP Service and Exchange Server", you require a single installation file named "EAExchDomainKeys.exe". Please download the latest DKIM installer from:
https://www.emailarchitect.net/webapp/download/eaexchdomainkeys.exe.
Double click this file, and read the license agreement carefully. If you agree to the terms, click "I agree" to proceed the installation. Otherwise click "Cancel" to abort the installation. "DomainKeys/DKIM for IIS SMTP Service and Exchange Server" requires IIS SMTP Service or Exchange Server to be installed and enabled. If no IIS SMTP Service or Exchange Server is detected in your operation system, the installer only installs DKIM management tool.
We strongly recommend that you have a look at the following tutorials based on your server environment.
DKIM in IIS SMTP
Service - Tutorial
DKIM in Exchange
Server 2003 - Tutorial
DKIM in
Exchange Server 2007/2010/2013/2016/2019 - Tutorial
DKIM in
Exchange Server SE (Subscription Edition) - Tutorial
Installation Permission
When you install EA DomainKeys on IIS SMTP server, please make sure you are using "Administrator" user to run the installer. If you install EA DomainKeys on Exchange Server, please make sure you are using "Domain Administrator" user to run the installer.To add DomainKeys/DKIM signature for outgoing email from a specified domain, you should open "DKIM Plugin Manager" from "Windows Start menu" -> "All Programs" -> "EA DKIM for IIS SMTP and Exchange Server" to begin the configuration, and then click "DomainKeys/DKIM -> New".
Important notice: DomainKeys/DKIM signature is based on the domain of sender email address, it is unrelated to the name of server.
For example, if you want to sign the email from *@emailarchitect.net, please input emailarchitect.net to Sender Domain.
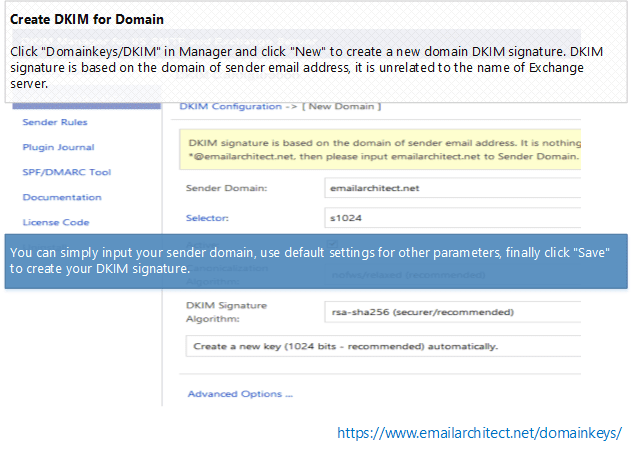
You can simply input your sender domain, use default settings for other parameters, finally click "Save" to create your DKIM signature.
Here is the detailed information about DKIM parameters:
| Parameter | Description |
| Sender Domain | DKIM signature is based on the domain of sender email address. It is nothing about your server name. For example, if you want to sign the email from *@emailarchitect.net, please input emailarchitect.net to Sender Domain. |
| Selector | To support multiple concurrent public keys per sending domain, the DNS namespace is further subdivided with "selectors". Selectors are arbitrary names below the "_domainkey." namespace. To learn more detail, please refer to Selector section. For a new domain, you can simply use the default value "s1024". |
| Active | If you have this option unchecked, DKIM for this domain will be disabled. |
| Canonicalization Algorithm | nofws/relaxed is recommended and it has better compatibility. |
| DKIM Signature Algorithm | On Windows 2000/2003/XP, rsa-sha1 is the only option. On windows vista/7/2008 or later version, you can choose "rsa-sha1" or "rsa-sha256". "rsa-sha1" gives better performance while "rsa-sha256" is more secure. "rsa-sha1" is recommended. |
| Signed Headers | Specify what message headers should be signed. "sender" header and "from" header are a MUST. Using default setting is recommended. |
| Sign only message headers | By default, DKIM signs entire body of message, however you can specify signing only the message headers. If your server relays message through a remote MTA, and this MTA adds disclaimer or changes email body content, I suggest that you enable this option. |
| Sign system message | By default, DKIM plugin doesn't sign system message, because those messages are supposed to transfer internally. However, if your server deliveries system message to internet, you should enable this option . |
| Sign internal MAPI message | By default, DKIM plugin doesn't sign internal MAPI message to grow the performance, buf if you need to delivery MAPI message to internet (this is not default behavior of Exchange server), you should enable this option. |
| Sign delivery report | This option specifies whether signing delivery report, default is true. |
| Sign only message headers for delivery report | If this option is enabled, DKIM signs only message headers if the message is delivery report. |
| Fix bad headers in embedded message | Sometimes, Exchange SMTP service wraps folded headers of embedded message again after DKIM signature is signed. This behavior may corrupt the message body hash. Enabling this option can fix this issue. |
| Wrap email address with <> in email header automatically. | Sometimes original email header doesn't wrap email address with <>, however after DKIM is signed, some relay MTA may wrap email address automatically, this behavior corrupts the DKIM signature. This option can avoid the problem. You don't have to check this option (performance issue) except the relay MTA corrupted the signature. |
| Disabled recipients | If message recipients contain the following email address, then disable DKIM signature. Please separate multiple addresses by line-break. Wildcard (* and ? ) is supported. |
After you added a domain in DKIM Plugin Manager, you can select the domain and click "Export Public Key". A dialog box will pop up and it will display a Public Key and a TEXT record for you to deploy in your DNS server.
>> Deploy public key in DNS server
You can synchronize the configuration files on multiple servers as follows:
Now, all of your servers have the same configuration (private/public key pair) for your domain.
To learn more detail, please refer to Selector section.
By default, EA DomainKeys installs an event sink "EA DomainKeys Sink" on your IIS SMTP (Exchange 2000 and Exchange 2003) OnPostCategorize event. With this event, EA DomainKeys Sink gives better performance. Be caution that if you have another SMTP plug-in that will change the message content after the DomainKeys signature was added, the signature will be interrupted.
You can also install the sink to OnMessageStart event manually with the following batch file. OnMessageStart event is almost the last event before IIS SMTP sending out an email to remote host. So installing EA DomainKeys Sink on this event has good compatibility with other SMTP plug-in software.
If you install EA DomainKeys on IIS SMTP Service, Exchange 2000, Exchange 2003, after completion you will find "InstallOnPostCategorize.bat" and "InstallOnMessageStart.bat" at EA DomainKeys installation folder\installer. You can double click the bat file to install EA DomainKeys on specified event sink.
You don't have to run the above batch files if you want to use default settings.
By default, EA DomainKeys installs a transport-agent "EA DomainKeys Agent" on Exchange 2007/2010/2013/2016/2019/SE. If you install another transport agent after EA DomainKeys was installed, the new transport-agent may interrupt the DomainKeys/DKIM signature. If you find the DomainKeys/DKIM signature is interrupted after you installed a new transport agent, you should simply re-run EA DomainKeys installer to fix this problem (not necessary to uninstall it), the installer will re-install your DomainKeys/DKIM agent to the last agent again and the DomainKeys/DKIM signature will not be interrupted by other transport agent.
Important Notice: If your server is Exchange 2007, you MUST have Exchange 2007 SP1 rollup 9 or SP2 installed on your server.
You can use silent installation on Windows 2016/2019/SE Server Core without desktop experience installed. To learn more detail, please go to Server Core and Installer Command Arguments.
You can use DkimPowerShell Module to manage DKIM, or you can use C#, VB.NET to manage DKIM programmingly. You can find the full sample project in DKIM installation path\DkimConfigSample
Does DKIM Plugin affect the performance of your server? In our test environment with 1000MB local LAN, when DKIM plugin is not installed, the SMTP service yields 30 emails (5KB) per second. After DKIM plugin is installed, the SMTP service yields 26-29 emails (5KB) per second (DKIM 3.5 yields 60 emails). In real world, there will have no notable difference in CPU usage (DKIM plugin only utilize CPU/Memory resources), because most idle CPU time is used to wait for remote server connection. You may consider DKIM plugin only utilizes the idle CPU time. In short, in real world, DKIM plugin take zero effect to the performance of your server.
To sign the DKIM/DomainKeys signature, DKIM plugin needs to read every email in your server. You may worry about that if DKIM software expose your company email to others. We always respect the customer privacy, and our DKIM plugin never connect or send content to network. DKIM plugin does not have network connection functions.
DKIM Plugin Manager will only connect to our server under the following situations:
Our DKIM Plugin never send your email content/server information to remote server.
>> Deploy Public Key in DNS server
>> Test DomainKeys/DKIM signature
>> Using Selector (If you have only one server, please skip this section and go
to Deploy
Public Key directly)
See Also
Deploy Public Key in DNS server
Test DomainKeys/DKIM signature
Troubleshooting
Using Selector
Using Sender Rule
Server Core and Installer Command Arguments
Appendix - Set up SPF record in DNS server
Appendix - Set up DMARC record
Appendix - DKIM/SPF/DMARC Inbound Authentication in Exchange Server
Appendix - Use DkimPowerShell Module in PowerShell
Online
DKIM in IIS SMTP
Service - Tutorial
DKIM in Exchange
Server 2003 - Tutorial
DKIM in
Exchange Server 2007/2010/2013/2016/2019 - Tutorial
DKIM in
Exchange Server SE (Subscription Edition) - Tutorial
DKIM/SPF/DMARC
Inbound Authentication in Exchange Server
Bulk Email Sender Guidelines
Check Services Status after Installation
- After the installation is complete, please check "Microsoft Exchange Transport Service" and "Microsoft Exchange Mail Submission Service" in Control Panel -> Administrative Tools -> Services, and make sure those services are running, if those service are not running, please start it.
- After the installation is complete, please check "IIS Admin" and "Simple Mail Transfer Protocol (SMTP)" in Control Panel ->Administrative Tools -> Services, and make sure those services are running, if those service are not running, please start it.
After the installation is complete, click "DKIM Plugin Manager" from " Windows Start menu -> All Programs -> EA DKIM for IIS SMTP and Exchange Server " to begin the setup.